
If you use LastPass, you might be concerned about its security breach.
The descriptions in some of the technical press can appear quite complex.
So here’s a simplified version of what happened.
LastPass Security Breach: What Happened?
A hacker stole some code and technical information from a LastPass development area (that’s an environment where the company does test and development work).
They used this to target a LastPass employee from where they could get access to credentials and keys.
These credentials and keys got the hackers access into LastPass’ third-party cloud storage service.
There they were able to decrypt some stuff.
And from that point, the hacker accessed and copied information from a cloud backup storage.
What Information was Accessed and Copied from LastPass?
It was things like basic customer account information and related metadata, including:
- Company names
- End-user names
- Billing addresses
- Email addresses
- Telephone numbers
- IP addresses from which customers were accessing the LastPass service
What Else Did The Hackers Get?
They were also able to copy a backup of customer vault data.
Thankfully, this was from the encrypted storage container.
So these were securely encrypted:
- Website usernames and passwords
- Secure notes
- Form-filled data
…although website URLs (website addresses) were not encrypted.
LastPass reassures us that they use hashing and encryption methods to protect customer data.
But they warn that the hackers might use “brute force” in an attempt to guess customers’ master passwords and decrypt the copies of data they stole.

Beware of a “brute force” attempt
What’s Brute Force – and What Can I Do?
According to Kaspersky…
A brute force attack uses trial-and-error to guess login info, encryption keys, or find a hidden web page. Hackers work through all possible combinations hoping to guess correctly.
The hackers don’t have everything they want. So beware of phishing. It probably isn’t going to be a real LastPass employee who rings you and asks you to confirm security details.
LastPass will never call, email, or text you and ask you to click on a link to verify your personal information.
Make sure your master password is too hard to guess. Make it complex and long: at least 12 characters including
- Uppercase and lowercase letters
- Numbers
- Special characters
What Difference Does a Strong Password Make?
Here’s a table that Hive Systems published in 2022, showing how long it would probably take to brute force your password.
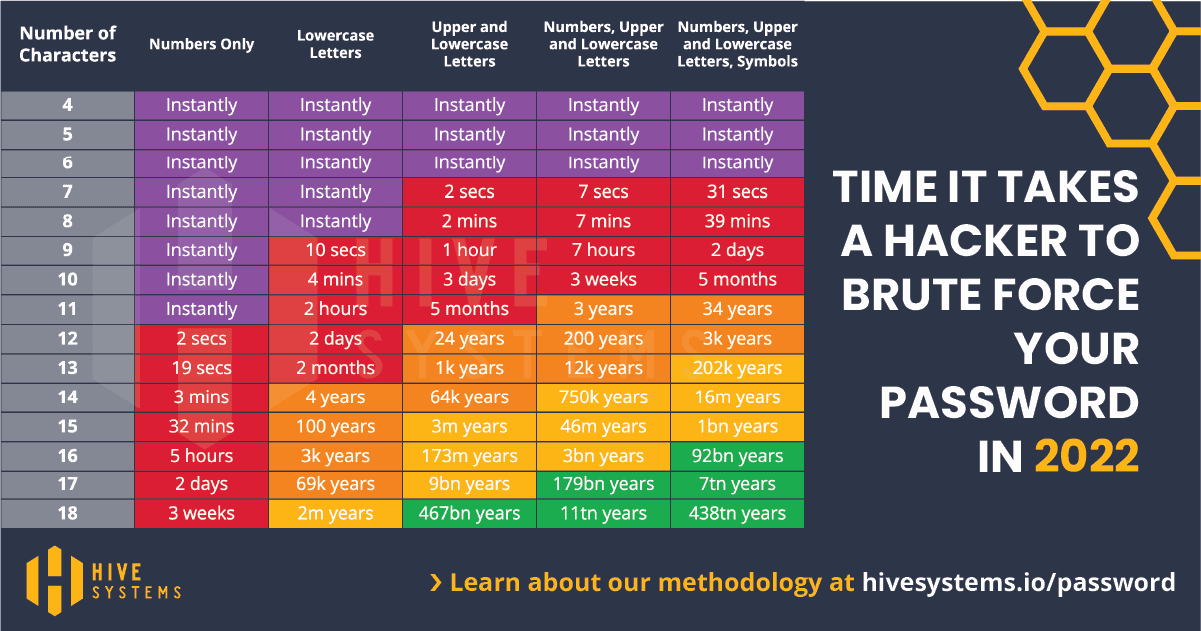
Estimated Time to Brute Force Passwords – Credit: hivesystems.io
So how secure are your passwords?
To reinforce a good master password, LastPass says they have a password-strengthening algorithm that makes it difficult to guess your master password.
But although LastPass assures us that, by following its best practices, it would take millions of years to guess your master password, some commentators still suggest changing it.
But definitely don’t use the same password anywhere else.
Oh, and for extra security, make sure to enable 2-factor authentication. That’s the sort of thing banks use nowadays to prove it’s really you. They send you a secret code (usually to your phone) which you need to enter before you can access your account.
By the way, if you don’t use LastPass’ default values in setting up your secure master password, they suggest changing all your passwords.
Here’s where you can read the LastPass statement in full, and learn how to make your master password more secure.
What Do The Experts Think?
We know what the media thinks. It’s all over the internet.
But what about the experts in that field?
I asked Richard Tubb, one of the best-known experts within the global IT Managed Service Provider (MSP) community. He says:
“In the current Cybersecurity landscape, it’s impossible not to be attacked. But it is how companies handle these breaches that speaks loudest. Do they downplay the impact and sweep it under the carpet, or are they open and honest in what has happened, what the impact is for customers, and what they’ve learned to prevent future attacks? I’m impressed with LastPass’ transparency”.
Richard Tubb
Richard Tubb launched and sold his own MSP business before creating a leading MSP media and consultancy practice. Richard helps IT Business Owners take back control by freeing up their time and building a business that can run without them. He’s the author of the book “The IT Business Owner’s Survival Guide” and writer of the award-winning blog: Tubblog.co.uk.
Conclusion
I hope this simplifies what happened in the LastPass password security breach.
And I hope it helps to clarify what it could mean to you if you use LastPass.
I’m not affiliated to LastPass – just a user. So I was just as concerned to read about it.
But I must agree with Richard Tubb – LastPass has been upfront about its breach and we know where we stand, unlike many companies who have suffered similar breaches.
I’m watching the developments with interest.
What are your thoughts? Will you continue to use LastPass or move to another?



Leave a Reply